Hackvertor EAN-13 and TOTP tags for web-application penetration testing with Burp
Hackvertor is a standalone tool and more importantly for us an extension for the penetration testing tool Portswigger Burp Suite by Gareth Heyes of the Portswigger Research team, which performs dynamic data conversions. For example, the tool can be used to encode data fields as Base64 before Burp sends a HTTP POST request to a server. This happens automatically and there is no need to manually convert anything or copy and pasting between different windows.
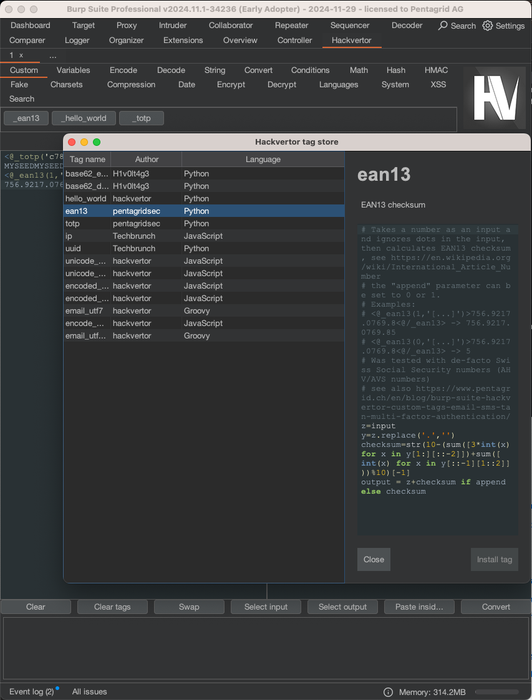
We had an example in our blog, where we generated Swiss social security numbers for a pentest and explained how to program custom Hackvertor tags. There are all kinds of tags already available inside Hackvertor and users can also code their own custom tags. Nowadays Hackvertor has it's own public tag store, where users can submit custom tags. Pentagrid provided two custom tags that made it into the Hackvertor tag store. One tag is for calculating the check-digit of EAN-13 numbers and another is for Time-based one-time password (TOTP) calculation.
As already explained in our blog post Teaching Burp a new HTTP Transport Encoding, being able to customise Burp like this is a helpful instrument to automate and increase test coverage during a security analysis.
EAN-13 Hackvertor tag
EAN is the European Article Number, a standard to encode article numbers. And while it became more international than European and is now called Global Trade Item Number, it is often still referred as EAN-13. Swiss AHV/AVS numbers use the check-sum calculation from EAN-13 and store the check-sum as the 13th digit.
The custom tag code from our blog post was made available as a Hackvertor tag in the tag store. To use the EAN-13 tag, see the following two examples:
# the "append" parameter can be set to 0 or 1. <@_ean13(1,'[...]')>756.9217.0769.8</@_ean13> # -> 756.9217.0769.85 <@_ean13(0,'[...]')>756.9217.0769.8</@_ean13> # -> 5
The omission [...] is the place where a so-called Hackvertor code execution key must be inserted. The Hackvertor Burp extension will add the code execution key automatically, if the tags are used and prepared in the Hackvertor tab in the Burp UI. The execution key is a random 40-hex character string that prevents websites processed by Burp from triggering harmful actions. The code execution key is unique to your Burp application start. Only code execution tags (with custom code such as the ones in the tag store) require code execution keys.
TOTP Hackvertor tag
Pentagrid also implemented a TOTP tag. This time-based one-time password is used for second factor authentication. If such a second factor is required during the penetration test, this Hackvertor tag can be used. The code was recently added to the tag store. To use the TOTP tag, extract the seed from the QR code that was handed over to you to scan it with an authenticator app. The command line tool zbarimg can dump QR code content from an image file:
% zbarimg ~/Authenticator-QR-Code.png QR-Code:otpauth://totp/SomeOrg:something?secret=MYSEEDMYSEED2342&issuer=SomeOrg scanned 1 barcode symbols from 1 images in 0.05 seconds
The tag can then be used analogue to this example:
There are several parameters for TOTP. In practise, the tag only supports the commonly used parameters SHA1, 30 seconds, 6 digits. Let us know if you find a different configuration in the wild, it should be fairly simple to adapt the custom tag in that case.
In order to access the tag store, just go to the menu entry "View tag store" from the Hackvertor menu in Burp and install the plugins you want. Then also make sure to allow code execution tags via the menu entry "Allow code execution tags" from the Hackvertor menu in Burp.
Update 2025-06-04: An update of Hackvertor in 2025 changed the style of closing elements from <@/name> to </@name>. Therefore, we updated the post.