Kiosk mode bypass for an Ariane Allegro Scenario Player based hotel check-in terminal
A threat modeling workshop took us to a remote location where there was a new hotel. It was so small that there was no check-in staff, but a check-in terminal for self-service. What was bound to happen, happened.
The hotel check-in terminal is running an Ariane Allegro Scenario Player in a kiosk mode and the application crashed when entering a single quote character into the guest search. The application crash allowed access to the underlying Windows Desktop. According to Ariane, an outdated software version was installed in the new hotel.
According to the vendor Ariane Systems, "Ariane is the world leader in providing self-check-in and out solutions for the hotel industry. [...] Ariane currently serves 3,000 hotels and 500,000 rooms in more than 25 countries. This includes one-third of the top 100 global hotel chains."
Timeline
2024-03-05: Vulnerability was discovered at a check-in terminal.
2024-03-06: Preliminary advisory written.
2024-03-06: Information sent to the hotel brand that uses the check-in terminal and asked about used application versions.
2024-03-07: Tried to find information how a vulnerability can be reported to Ariane Systems. The vendor does not use security.txt nor a DNS TXT record for security contact lookup. There is no information on the website how to contact the product security team. Therefore, Pentagrid initially contacted Ariane Systems via support@ariane.com.
2024-03-14: Sent another request to the Ariane Systems support, after not receiving any feedback.
2024-03-14: Sent a status information to the affected hotel.
2024-03-14: Contacted Ariane Systems' technical leader and chief product officer via Linkedin. Chief product officer responded and recommended to contact dataprivacy@ariane.com.
2024-03-14: Sent e-mail to dataprivacy@ariane.com.
2024-03-14: Verified all e-mails of previous communication attempts were received by Ariane Systems' mail server by reviewing Pentagrid's mail server logs.
2024-03-15: Tried to get an e-mail receipt confirmation from the chief product officer via Linkedin, after not receiving any feedback.
2024-03-18: Tried to contact chief product officer via e-mail by guessing the e-mail address, after not receiveing any response, but e-mail address guessing failed.
2024-03-18: Contacted chief product officer via Linkedin again, to get a confirmation that Pentagrid's e-mail for starting the coordinated disclosure process has been received.
2024-03-18: Contacted Ariane Systems publicly via Linkedin.
2024-03-18: Sent vulnerability details to dataprivacy@ariane.com, after getting a first contact confirmation via e-mail.
2024-03-18: Received first response, which stated that the systems are legacy systems, that USB ports are disabled and "no PII or exploitable data can be retrieved from the kiosk".
2024-03-25: Disputing Ariane Systems' claim that no PII data can be retrieved, because as part of the system design the kiosk produces and keeps accessible invoice files.
2024-04-11: Call with Ariane Systems.
2024-05-31: Asked Ariane for a status, but there was no response.
2024-06-05: Publication after 90 days.
2024-06-06: CVE-2024-37364 was assigned.
Kiosk mode bypass
CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H, 6.8 Medium
Affected Components
The check-in terminal is likely a terminal of type Ariane Duo 6000 series, which runs the Ariane Allegro Scenario Player.
A hotel brand from Liechtenstein and Switzerland uses the check-in terminal for smaller hotel locations. The check-in terminal supports room booking as well as checking into the hotel. It initiates the payment process via a POS terminal, provisions RFID transponders to open the booked hotel room and it prints an invoice.
Summary
The check-in terminal allows searching for existing room reservations. Reservations can be looked up by booking code or by surname. When searching a reservation by name and the entered name contains a single-quote, the application hangs. When touching the screen of the terminal again, the Windows operating system will ask the user if Windows should wait any longer or stop the task. Selecting stop ends the kiosk mode application.
Impact
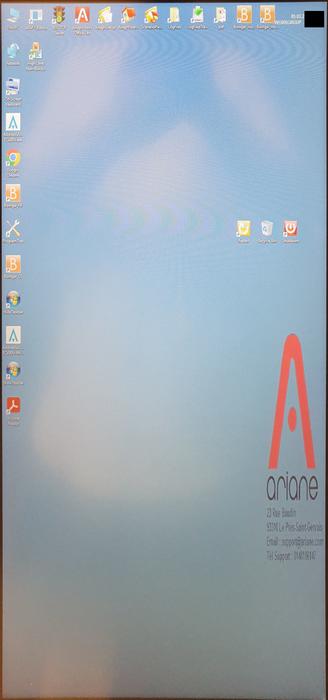
When stopping the application, the kiosk mode is stopped and the user gets access to a Windows desktop.
With access to the Windows desktop, attacks on the hotel network could become possible as well as access to data stored on the terminal, which includes PII, reservations and invoices. With the ability to inject and execute program code, it seems possible to get room keys created for other rooms, because the functionality of provisioning RFID transponders is implemented in the terminal.
Technical Details
When a user searches an existing reservation and adds a single-quote to the surname, the application hangs. An example input that causes the effect is "O'YOLO".
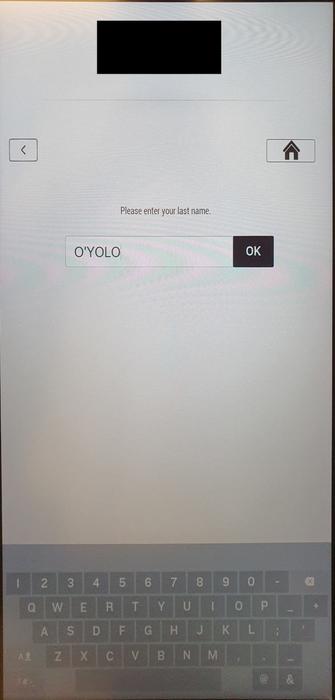
The application hangs. By touching the Elo display again, Windows will ask how to proceed with the application.
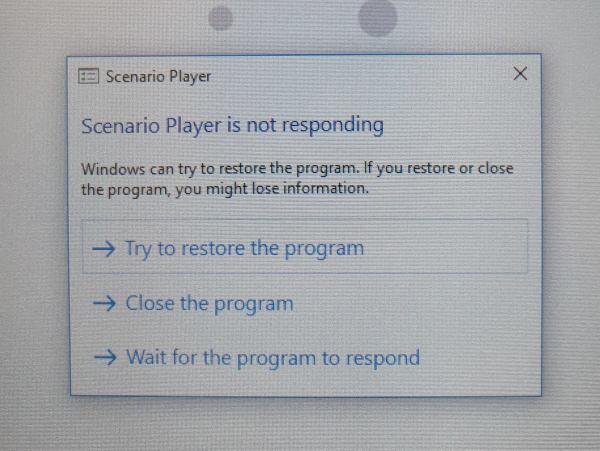
When stopping the application, the Windows desktop becomes accessible.
Precondition
An attacker needs physical access to a check-in terminal and depending on the attack preparation some time at the terminal. The terminal must be in a state where it allows self-service, for example as Hotels might only enable it during specific times.
Recommendation
According to Ariane, the problem was fixed in the Allegro Scenario Player. Therefore, Pentagrid recommends hotels using the terminal:
To ensure that a recent version of the software is installed. The version that fixes the issue is not known to Pentagrid. Hence Ariane Systems should be asked.
To isolate check-in terminals so that bypassing the kiosk mode does not allow attacks on the hotel network or the Windows domain.
Credits
This vulnerability was accidentally found by Martin "O'YOLO" Schobert (Pentagrid).